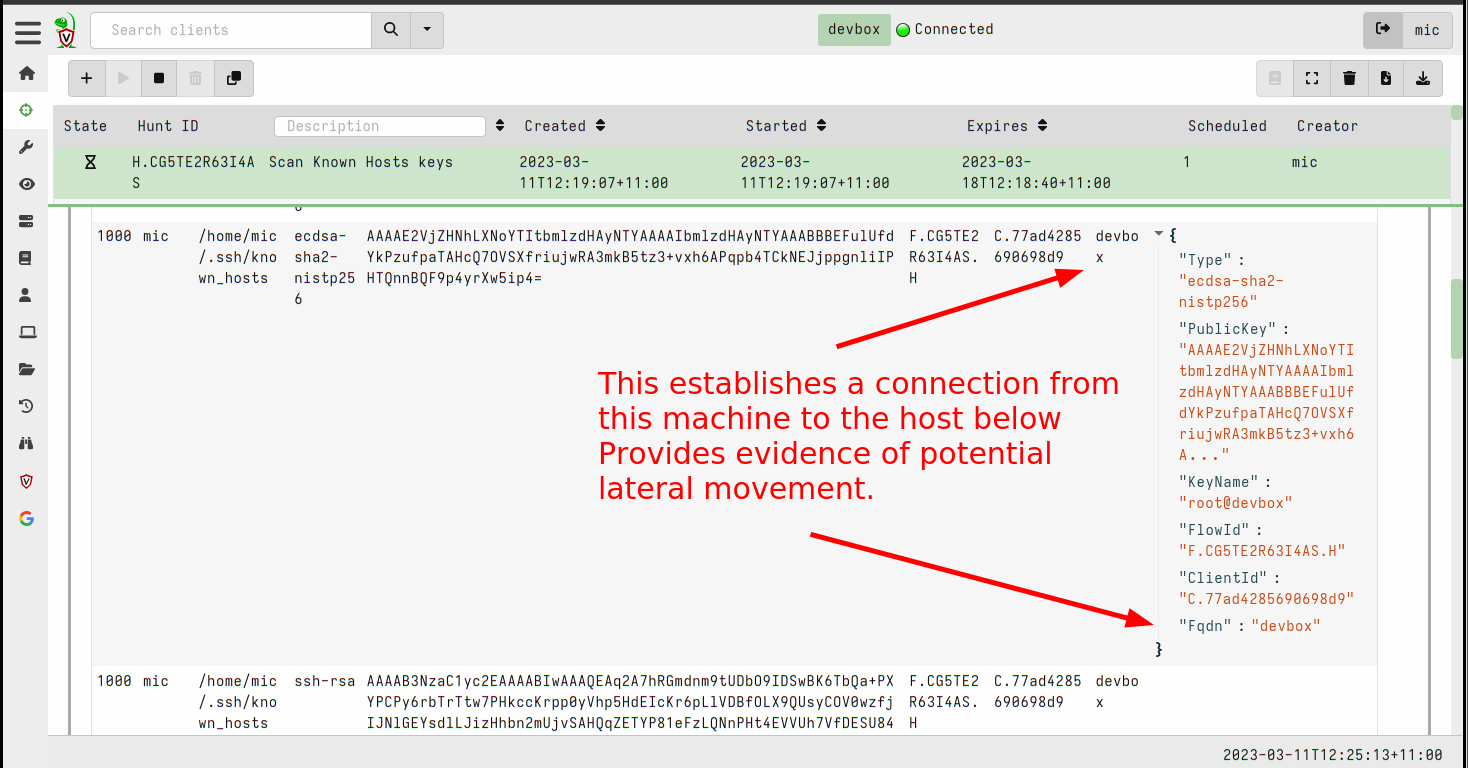
<!-- .slide: class="title" --> ## Secure Shell ### Linux remote access  --- <!-- .slide: class="content" --> ## Secure Shell ### Linux remote access On Unix like systems, remote administration is usually done using Secure Shell (SSH) * Authentication is usually decentralized: * Username/Password based * Public/Private key based --- <!-- .slide: class="content" --> ## Secure Shell ### Linux remote access * Authorization is usually achieved in a decentralized way * `~/.ssh/authorized_keys` file lists all keys allowed to log in to this machine. * `~/.ssh/known_hosts` file list all hosts known to this user (that the user has logged into previously). --- <!-- .slide: class="content" --> ## Typical SSH based attacks 1. A user account with password auth is compromized on an endpoint. 2. This gives the attacker a foothold on that host. 3. Unsecured ssh keys can be used on that host to log into other hosts 4. When the attacker logs into the other hosts they may change their user account --- <!-- .slide: class="content" --> ## Typical SSH escalation path 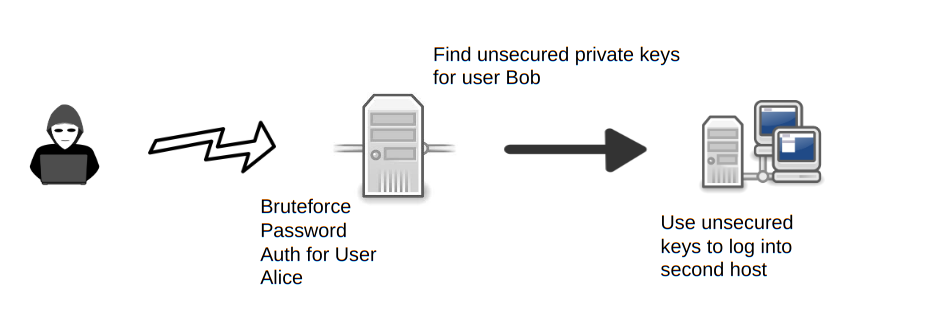 --- <!-- .slide: class="content" --> ## Investigative steps ### Search for password login Search the SSH logs for successful login using a password. This should not be common in practice! 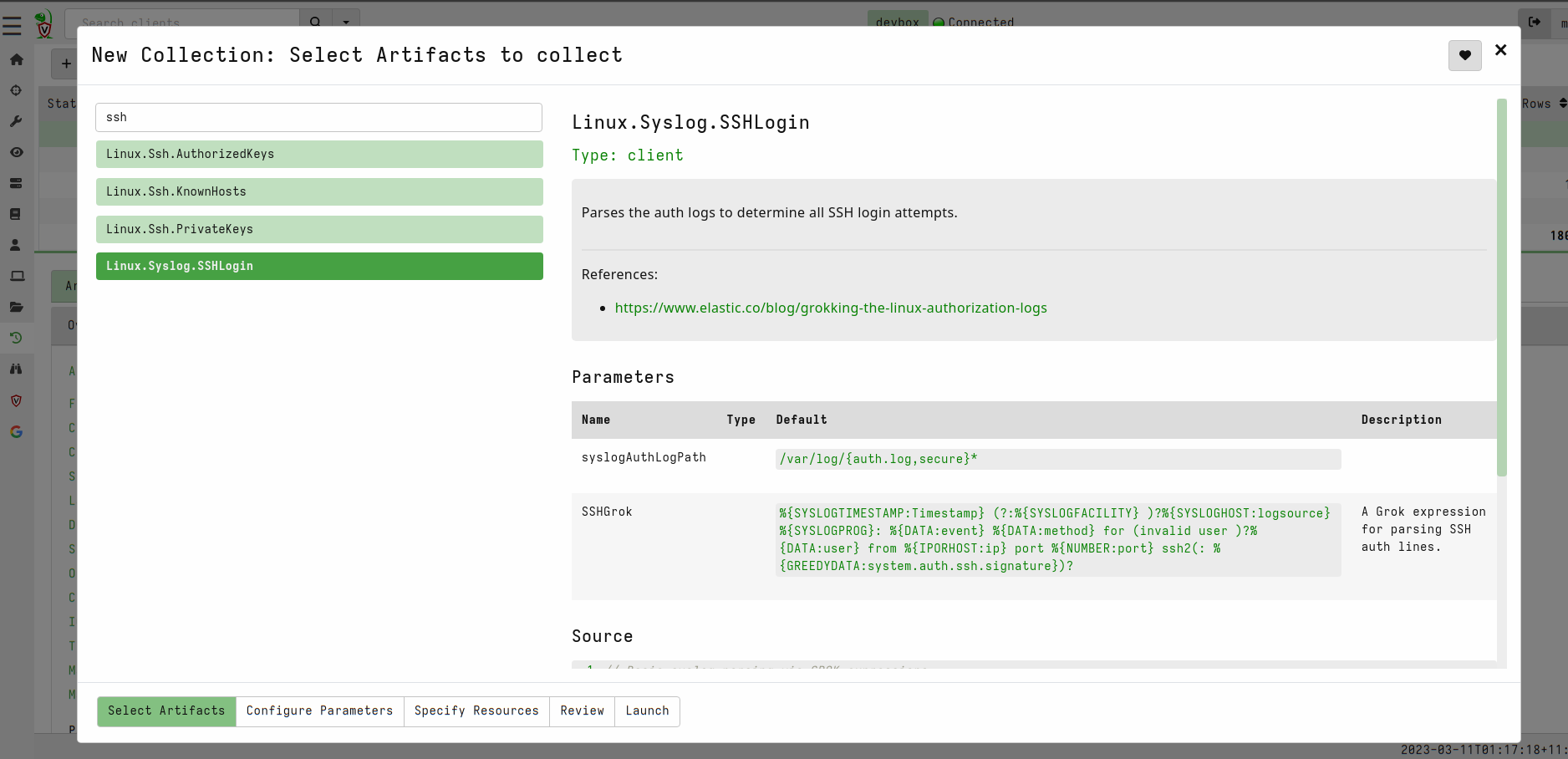 --- <!-- .slide: class="content" --> ## Investigative steps ### Find successful password logins 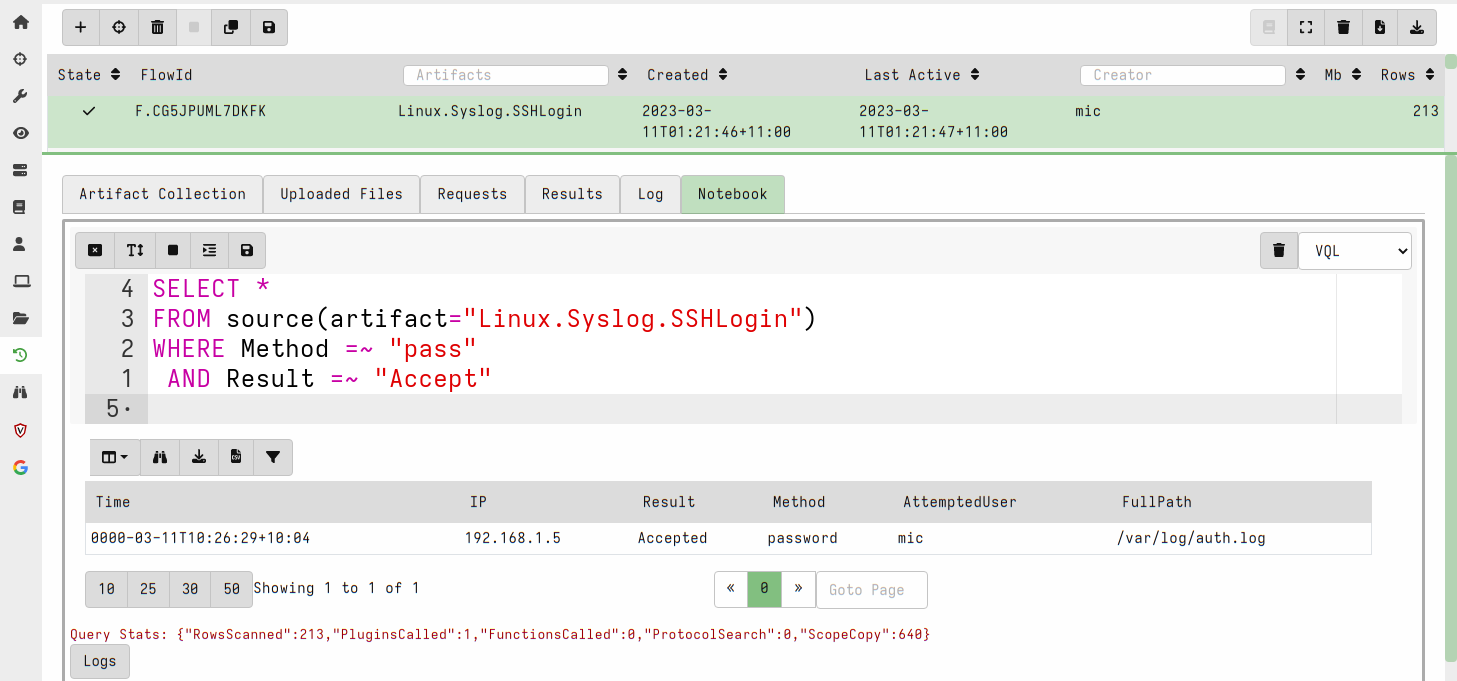 --- <!-- .slide: class="content" --> ## Investigative steps ### Did any of our hosts have unsecured keys?  --- <!-- .slide: class="content" --> ## Investigative steps ### Which machines trust the unsecured key? SSH uses the `authorized_keys` file to grant access to trusted keys. To find all machines that might grant access to this key we need to check that file everywhere. This is called a `Hunt` --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Hunt for Authorized Keys  --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Select artifact to collect  --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Start hunt  --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Post process hunt in VQL Notebook  --- <!-- .slide: class="content" --> ## Investigative steps ### Did the key actually get used? We can determine if any machine account was used to log into another host using the `known_hosts` file. This file records the hostname and host public key that were used in the past If we find the vulneable machine was logged into this might mean the vulnerable key was used. Unfortunately the hostname is hashed!!! --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Hunt for known hosts  --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Post-process hunt to match hostnames  --- <!-- .slide: class="content" --> ## Investigative steps - Hunt ### Establishing peer relationships